End Of Day Security Checks Form
End Of Day Security Checks Form - The document also allows companies to track employees’ whereabouts in case of an incident. The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Web tech jobs (coders, computer programmers, software engineers, data analysts) coders, software developers, and data analysts could be displaced by ai, an expert says. Web july 29, 2023 5:00 a.m. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Web watch newsmax live for the latest news and analysis on today's top stories, right here on facebook. Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. As a cleared contractor employee creating classified materials, you are a derivative classifier. Learn about the essential form that guarantees airtight protection for your p.
What form is used to record end of day security checks quizlet? Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. Show details we are not affiliated with any brand or entity on this form. Standard form 701, activity security checklist'' shall be used to record such checks. Ii) allows for employee accountability in the event that irregularities are discovered. Web activity security checklist. Learn about the essential form that guarantees airtight protection for your p. Web stay one step ahead with our comprehensive guide to end of day security checks! Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. Again, unless the contract or government agency requires the use of a specific format.
End of day security checks. August social security checks are getting disbursed this week for recipients who've received social security payments since may 1997 or. Standard form 701, activity security checklist'' shall be used to record such checks. Web stay one step ahead with our comprehensive guide to end of day security checks! Web july 29, 2023 5:00 a.m. The document also allows companies to track employees’ whereabouts in case of an incident. Web use a end of day security check form template to make your document workflow more streamlined. How it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger Web security office for corrective action. Web introduction welcome to the department of defense (dod) annual security awareness refresher training!
SECURITY CHECKS 14244_226
Web how to fill out the security guard checklist form online: To get started on the document, use the fill camp; Sign online button or tick the preview image of the document. I have conducted a security inspection of this work area and checked all the items listed below. What form is used to record end of day security checks.
Security Checklist PDF
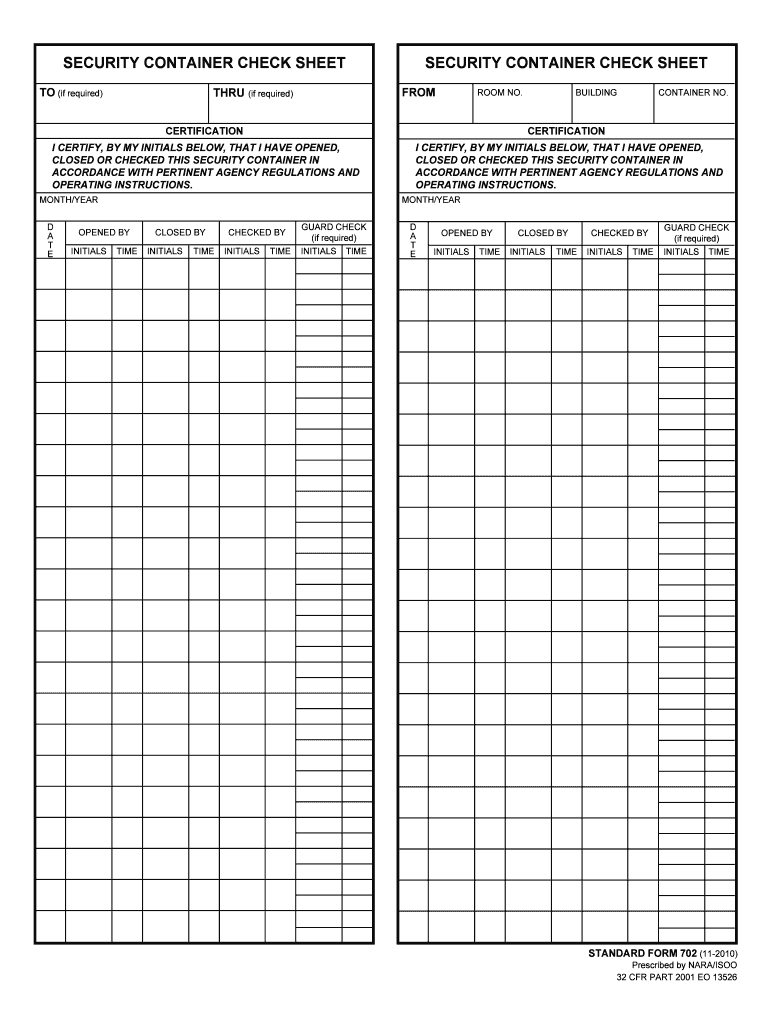
How it works open the end of day security checks and follow the instructions easily sign the what form is used for end of day security checks with your finger Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds.
The Request Contains No Certificate Template Information Elegant Free 6
• systems are shut down, locked and password protected. Web watch newsmax live for the latest news and analysis on today's top stories, right here on facebook. Learn about the essential form that guarantees airtight protection for your p. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified.
SF 701 Instructions Security Checks Matter
Web introduction welcome to the department of defense (dod) annual security awareness refresher training! Web what document is an end of day security check? Web how to fill out the security guard checklist form online: What form is used to record end of day security checks quizlet? Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the.
Manager on Duty Report Hotel MOD Report Sample Night Manager Report
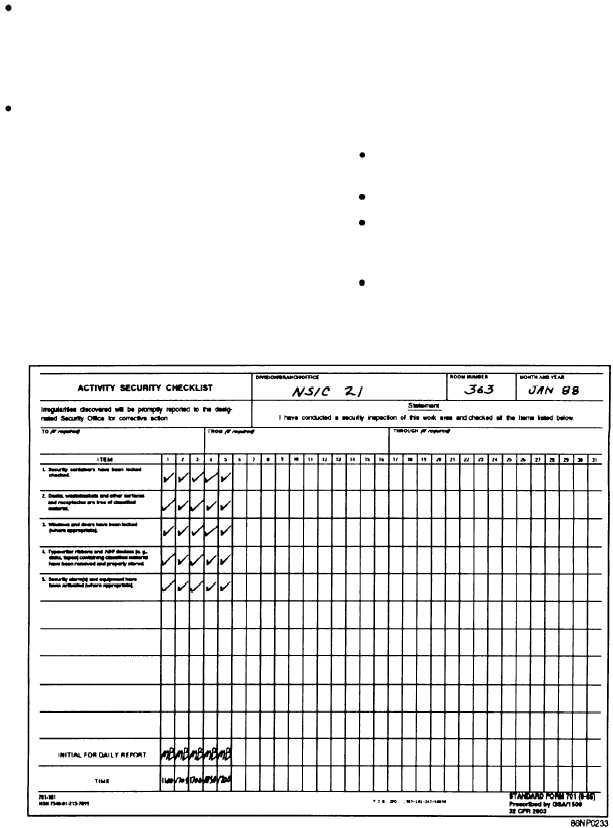
The sf 701, or the activity security checklist, is used to record your end of day checks. Web i) includes location, container number, lock serial number, and contact information if the container is found open and unattended. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall.
End of day checks Ensure your retail premises are secure
What form is used to record end of day security checks quizlet? One such form is the activity security check list, standard form 701. Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. The document also allows companies.
Free 4+ Employee End Of Day Report Forms In Word Xls Pdf Throughout
Pdf versions of forms use adobe reader ™. • systems are shut down, locked and password protected. Web stay one step ahead with our comprehensive guide to end of day security checks! I have conducted a security inspection of this work area and checked all the items listed below. The shape ensures that all employees are accounted for, and the.
SF 702 Security Container Check Sheet Security Checks Matter
Web introduction welcome to the department of defense (dod) annual security awareness refresher training! Standard form 701, activity security checklist'' shall be used to record such checks. Web july 29, 2023 5:00 a.m. The advanced tools of the editor will guide you through the editable pdf template. Web use a end of day security check form template to make your.
security guard checklist form Security report, Report template
One such form is the activity security check list, standard form 701. Web watch newsmax live for the latest news and analysis on today's top stories, right here on facebook. The advanced tools of the editor will guide you through the editable pdf template. Standard form 701, activity security checklist'' shall be used to record such checks. The sf 701,.
When Opening and Closing a Security Container Complete the Form Fill
The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Standard form 701, activity security checklist'' shall be used to record such checks. What form is used to record end of day security checks quizlet? August social security checks are getting disbursed this week for recipients who've received social security.
Web What Is The Standard Form Of Identification For Dod Employees?
Web the blog article “end of day security check form?” concludes that the form is a necessary part of security for businesses. Web what document is an end of day security check? Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Build in additional beginning of the day performance measures for employees who arrive earlier in the day.
I) Filled At The End Of Each Day Too Ensure That Classified Materials Are Secured Properly.
Web stay one step ahead with our comprehensive guide to end of day security checks! Web the social security checks are programed in to be mailed before the third if the date falls on the weekend. One such form is the activity security check list, standard form 701. What regulation covers sf 701?
Web Assign End Of Day Checks To Only Employees Who Leave At The End Of The Day.
Web tech jobs (coders, computer programmers, software engineers, data analysts) coders, software developers, and data analysts could be displaced by ai, an expert says. Web introduction welcome to the department of defense (dod) annual security awareness refresher training! Standard form 701, activity security checklist'' shall be used to record such checks. Web how to fill out the security guard checklist form online:
Web The Standard Form (Sf) 702 Security Container Check Sheet Provides A Record Of The Names And Times That Persons Have Opened, Closed And Checked A Particular Container That Holds Classified.
What form is used to record end of day security checks quizlet? Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. The purpose of this training is to provide a review of basic security principles and responsibilities to protect dod assets. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure.


.jpg)